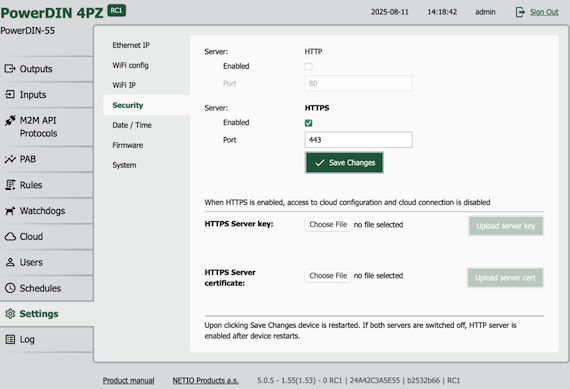
HTTPs details
Contents
HTTPS (Hypertext Transfer Protocol Secure)
HTTPs is the secure version of HTTP, the protocol used for communication between a web browser or application and a web server or device. HTTPS adds a layer of encryption using TLS (Transport Layer Security), which protects the data transmitted over the network.
Why Use HTTPs with NETIO Power Devices?
NETIO devices often operate in environments where they are remotely controlled or monitored, sometimes even over public or shared networks. Using HTTPS ensures that communication between your application and the NETIO device remains private and secure, even if someone intercepts the network traffic.
How to enable HTTPs on NETIO Device
All NETIO devices running on FW 5.0.X can be configure the way to support HTTPs communication. HTTPs option is available via Setting/ Security. Port 443 is pre-defined, but can be changed. HTTPs configuration port is shared with M2M API protocols setup. NETIO devices support HTTPs using a self-signed certificate by default. This allows you to use secure connections immediately, even in isolated or internal networks. For production environments or public access, is recommended to upload a certificate from a trusted Certificate Authority (CA). This ensures proper validation and avoids browser or client warnings.
TLS Versions and Cipher Suites Supported by NETIO
NETIO power devices support encrypted HTTPS communication using the TLS (Transport Layer Security) protocol. TLS ensures confidentiality, integrity, and authentication when accessing the device’s web interface or APIs (e.g., JSON/XML REST API).
Supported TLS Versions.:
- TLS 1.0 and TLS 1.1 – (Deprecated for security reasons)
- TLS 1.2 (Supported) (minimum secure standard and should always be used).Legacy TLS versions are disabled by default for security.
- TLS 1.3 – Not supported at the moment* (future development under investigation)
NETIO firmware supports multiple cipher suites using RSA or ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) key exchange, combined with AES encryption (GCM/CCM) modes. There is a list of supported TLS cipher suites and key types that NETIO devices accept when establishing a secure HTTPS connection.
Key Types used during the TLS handshake:
- ecc_prime256v1 – elliptic curve (ECDSA) key, 256-bit (NIST P-256)
- ecc_secp384r1 – stronger ECC key, 384-bit
- ecc_secp521r1 – even stronger ECC key, 521-bit
- rsa_1024 / rsa_2048 / rsa_3072 / rsa_4096 – RSA keys of corresponding lengths
Cipher Suite – a specific combination of algorithms used to encrypt the TLS connection:
- ECDHE – key exchange algorithm (supports forward secrecy)
- ECDSA – digital certificate based on ECC key (e.g., prime256v1)
- AES_256_GCM – symmetric encryption (AES 256-bit, Galois/Counter Mode)
- SHA384 – hashing algorithm used for integrity checks
List of combinations tested with NETIO device
|
-> ecc_prime256v1
|
-> ecc_secp384r1
|
-> ecc_secp521r1
|
|
|
-> rsa_1024
|
-> rsa_2048
|
-> rsa_3072
|
-> rsa_4096
|
Secure M2M API Access via HTTPs
NETIO devices support secure communication over HTTPS to protect API access to power sockets and configuration interfaces. This is essential when integrating NETIO devices with 3th party systems. M2M API Machine protocols setup uses the same port as being setup at configuration setting. Device provide access to various machine-readable APIs, such as:
- JSON API
- XML API
- MQTTs (optional for some models)
- URL
As HTTPS is enabled, all communication with these APIs is encrypted using TLS (Transport Layer Security). This ensures that authentication tokens, control commands (e.g., socket ON/OFF), and monitoring data cannot be intercepted or altered.
Here is an examples of turning socket 1 ON using the JSON API over HTTPS:
curl -k netio_user:netio_password -d '{"Outputs":[{"ID":1,"Action":1}]}' -H "Content-Type: application/json" -X POST https://192.168.105.160:81/netio.json
- (**Replace netio_user & netio_password with proper JSON API password)
Here is an example of turning socket 1 ON using URL over HTTPS:
https://192.168.1.100/netio.json?pass=netio123&output1=1"
- (**Replace netio123 with your actual API password)
API Performance testing
In internal NETIO testing on PowerPDU 4KS device (see below), various cipher suites and elliptic curves were evaluated for performance during secure HTTPS communication with the JSON and WebSocket APIs.
| Response time Web Socket [s] | Response time JSON [s] | |
|---|---|---|
| ecc_prime256v1 | ||
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 | 5.7 | 6.0 |
| TLS_ECDHE_ECDSA_WITH_AES_256_CCM | 5.9 | 5.6 |
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 | 5.8 | 5.7 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CCM | 6.1 | 6.2 |
| ecc_secp384r1 | ||
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 | 6.4 | 6.3 |
| TLS_ECDHE_ECDSA_WITH_AES_256_CCM | 6.3 | 6.2 |
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 | 6.2 | 6.2 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CCM | 6.5 | 6.3 |
| ecc_secp521r1 | ||
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 | 6.5 | 6.4 |
| TLS_ECDHE_ECDSA_WITH_AES_256_CCM | 6.6 | 6.5 |
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 | 6.7 | 6.3 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CCM | 6.6 | 6.5 |
* values are valid for ethernet connection only
** values can differentiate on WiFi connection